Forcepoint Cloud Security Gateway and VMware SD-WAN by VeloCloud
Table of contents
License
These contents are licensed under Apache License, Version 2.0. http://www.apache.org/licenses/LICENSE-2.0
TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE LAW, THE SITE AND ITS CONTENT IS PROVIDED TO YOU ON AN “AS IS,” “AS AVAILABLE” AND “WHERE-IS” BASIS. ALL CONDITIONS, REPRESENTATIONS AND WARRANTIES WITH RESPECT TO THE SITE OR ITS CONTENT, WHETHER EXPRESS, IMPLIED, STATUTORY OR OTHERWISE, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NON-INFRINGEMENT OF THIRD PARTY RIGHTS, ARE HEREBY DISCLAIMED
Document Revision
| Version | Date | Author | Notes |
|---|---|---|---|
| 0.1 | 02 October 2020 | Mattia Maggioli | First draft |
| 0.2 | 21 October 2020 | Jonathan Knepher | Review |
| 0.3 | 22 October 2020 | Mattia Maggioli | Minor updates |
| 0.4 | 16 November 2020 | Mattia Maggioli | Minor updates |
| 0.5 | 20 November 2020 | Jaspreet Bhatia | Updated “Configure VeloCloud Orchestrator – Edge” chapter |
| 0.6 | 25 November 2020 | Mattia Maggioli | Added co-branding items and minor updates |
Summary
This guide provides step by step instructions to integrate Forcepoint Cloud Security Gateway and VMware SD-WAN by VeloCloud so that Internet-bound web traffic flowing over the SD-WAN layer is filtered by Forcepoint Cloud Security Gateway according to customizable security policies.
The instructions provided in this guide enable system administrators to:
-
Configure VeloCloud Orchestrator to connect and route web traffic to Forcepoint Cloud Security Gateway using either a VeloCloud Gateway or an Edge device.
-
Configure Forcepoint Cloud Security Gateway to connect to VMware SD-WAN and apply web security policies to traffic received from VeloCloud.
A description of the workflow between the components involved in this POC is depicted in this diagram:
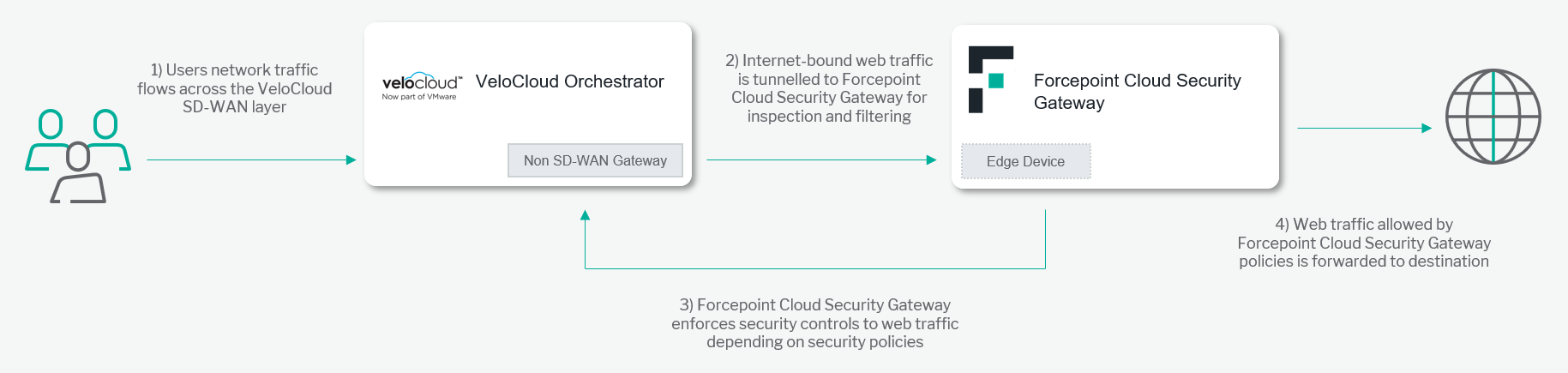
Requirements
The integration described in this document was developed and tested with the following products as of September 2020:
-
Forcepoint Cloud Security Gateway
-
VMware SD-WAN by VeloCloud 4.0
No other software or physical device is needed to integrate Forcepoint Cloud Security Gateway and VMware SD-WAN by VeloCloud. This document assumes both products are already installed and configured. For further information refer to the official documentation of both products:
-
Forcepoint Cloud Security Gateway: https://frcpnt.com/csg-documentation
-
VMware SD-WAN by VeloCloud: https://docs.vmware.com/en/VMware-SD-WAN-by-VeloCloud/index.html
Configure Forcepoint Cloud Security Gateway
A configured Edge Device is necessary to route traffic from VMware SD-WAN by VeloCloud to Forcepoint Cloud Security Gateway for inspection and filtering.
To create a new Edge Device in Forcepoint Cloud Security Gateway, follow these steps:
-
Login to Forcepoint Cloud Security Gateway using an account with administrative privileges.
-
Go to Web > Device Management, click the drop-down icon under the headline and select Add Edge Device.

-
In the Tunneling Type window select IPsec Advanced and populate the fields in the following page as follows
-
Name: use a descriptive name to identify the connection of this Edge. In our example we used Forcepoint_Tunnel01
-
Device type: select VeloCloud from the drop-down menu
-
Description: this field can be used for providing further details
-
IKE version: select IKEv2
-
IKE identity: select DNS and enter a DNS name within your namespace that will be configured also on the VeloCloud side in the next chapter. In our example we used test.customer02.com
-
Pre-shared key: select Use your own key and enter the same key that will be used on the VeloCloud side. In our example we used Velocloud321
-
Data Centers: from the list of Available data centers pick two which are closest to the location of the VeloCloud Edge device (so that latency will be minimal) and move them to the Selected data centers list. In our example we used United States – San Jose (G) and United States – Ashburn (H) since the VeloCloud Gateway is deployed in the United States.
-
Policy Assignment: from the drop-down menu select a default policy that will be applied to all traffic coming from the VeloCloud Edge device. In our example we left the DEFAULT policy.
-
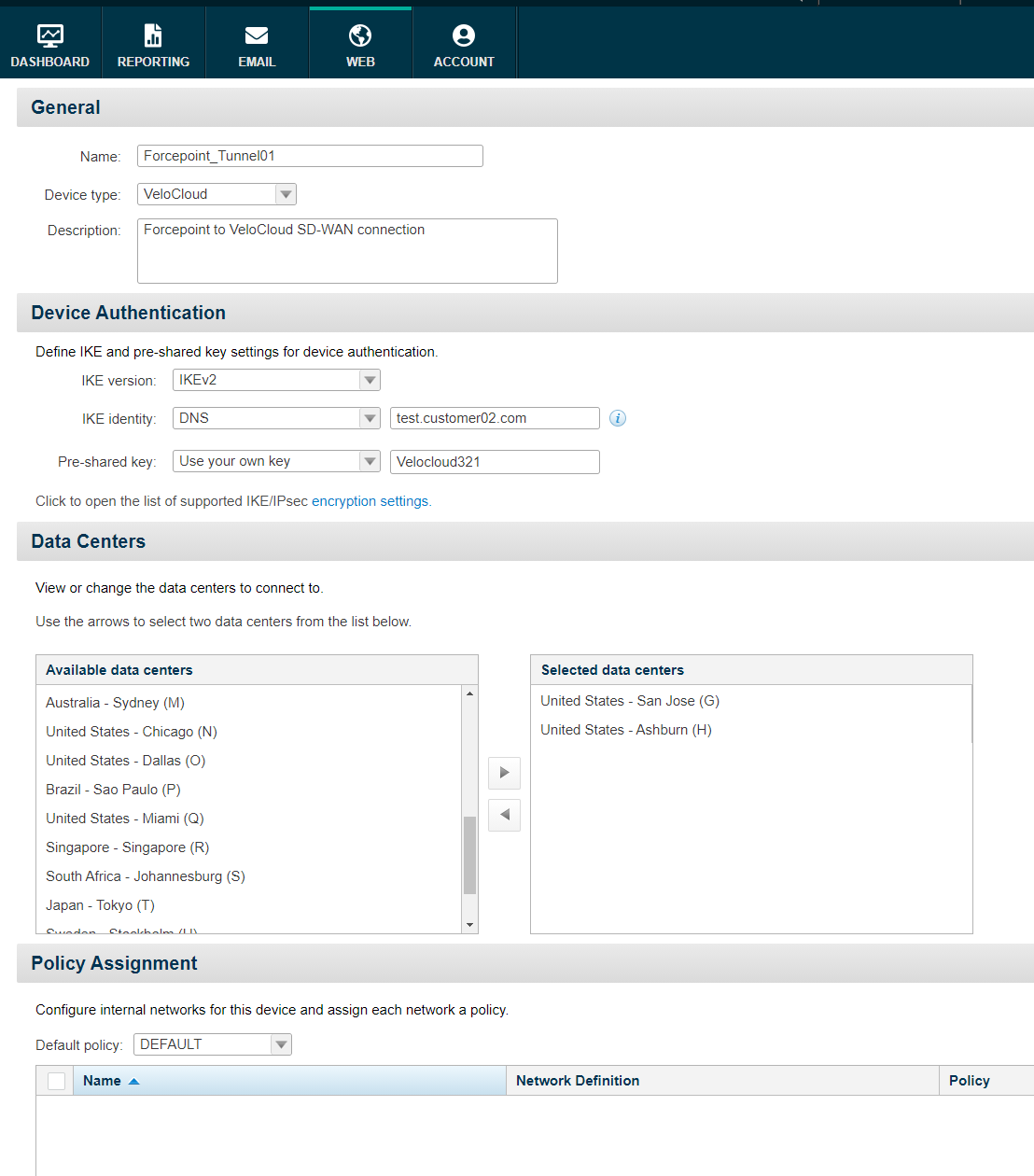
-
Click Save once done.
-
Back in the Device Management page, select the newly created Edge Device and note the Service IP of both Data Centers from the Status menu on the right side of the page, as they will be needed when configuring the VeloCloud side.
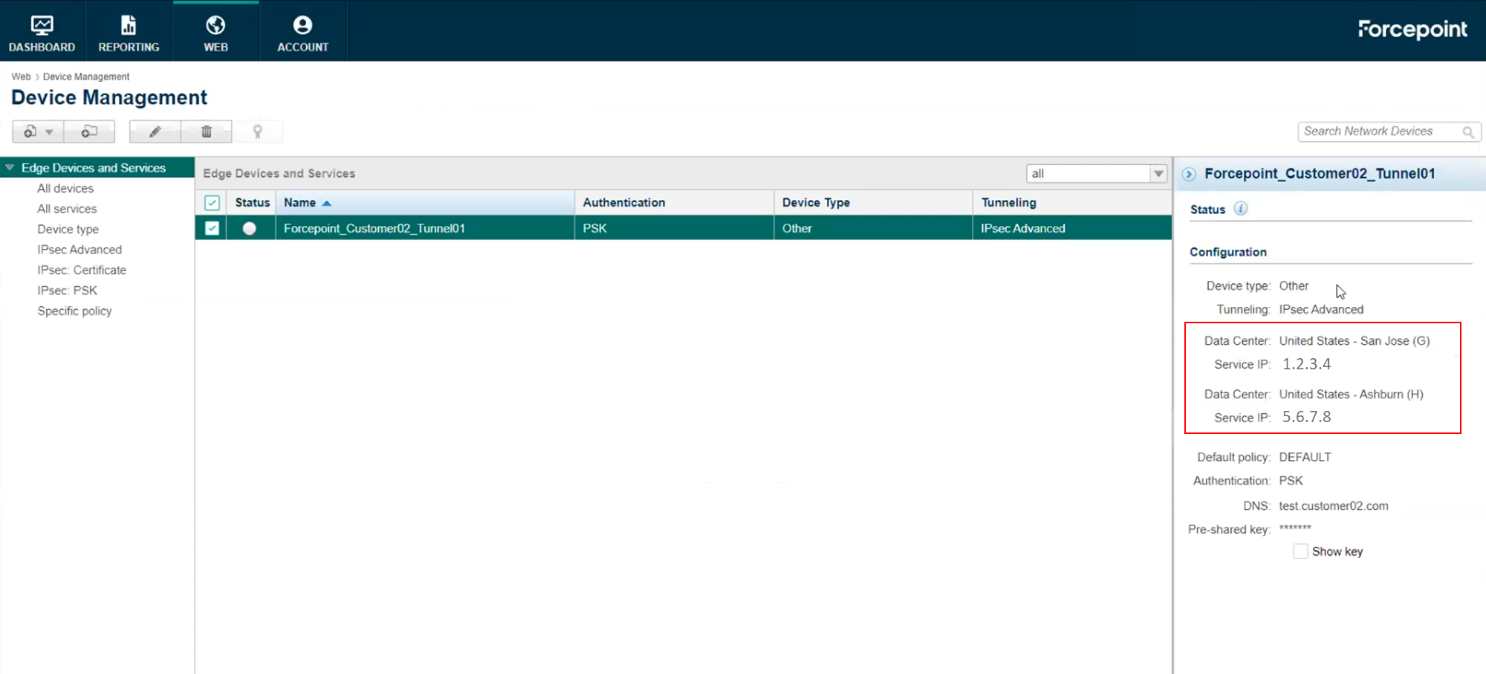
The Edge Device on Forcepoint Cloud Security Gateway side will wait for connections initiated by the VeloCloud Gateway.
Configure VeloCloud Orchestrator - Gateway
This chapter contains instructions to configure all components of the SD-WAN layer of VeloCloud Orchestrator using a Gateway as the endpoint for the tunnels between VeloCloud and Forcepoint Cloud Security Gateway. It is assumed that a Customer is already configured.
Move to the next chapter if you want to connect to Forcepoint Cloud Security Gateway using an Edge device.
Create new NSD Tunnel via Gateway
- Login to VeloCloud Orchestrator using an account with administrative privileges
- Click Manage Customers then click the Customer whose traffic will be route to Forcepoint Cloud Security Gateway
-
Click Configure > Network Services then move to the Non SD-WAN Destinations via Gateway and click New…
-
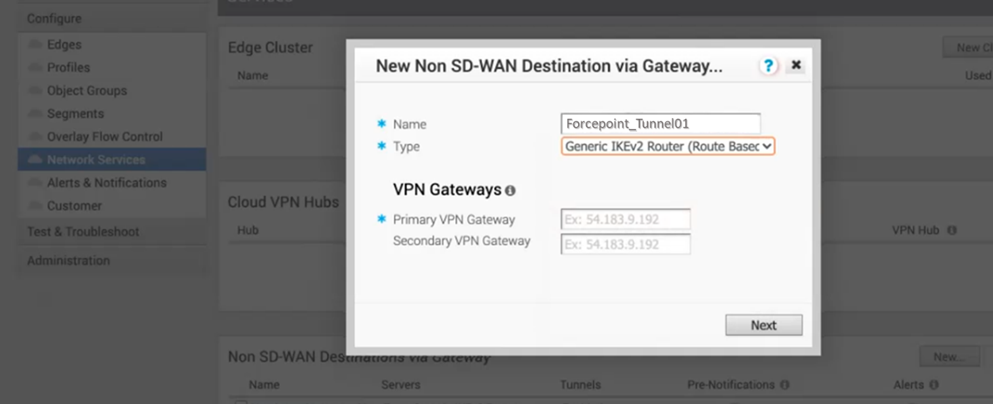
in the New Non SD-WAN Destinations via Gateway window enter the following parameters:
-
Name: a descriptive name for the Gateway
-
Type: select Generic IKEv2 Router
-
Primary VPN Gateway: fill this field with the IP address of the 1st data center from the Forcepoint Cloud Security Gateway Edge Device configuration. In our example we used 1.2.3.4
-
Secondary VPN Gateway: fill this field with the IP address of the 2nd data center from the Forcepoint Cloud Security Gateway Edge Device configuration. In our example we used 5.6.7.8
Once done click Next.
-
- The Gateway will be created within a few seconds.
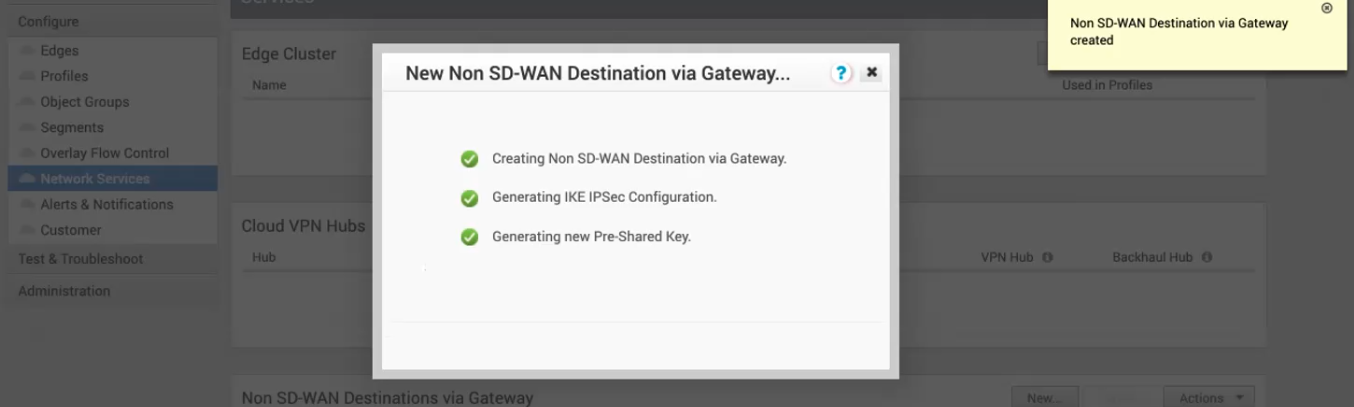
- In the next window click Advanced.
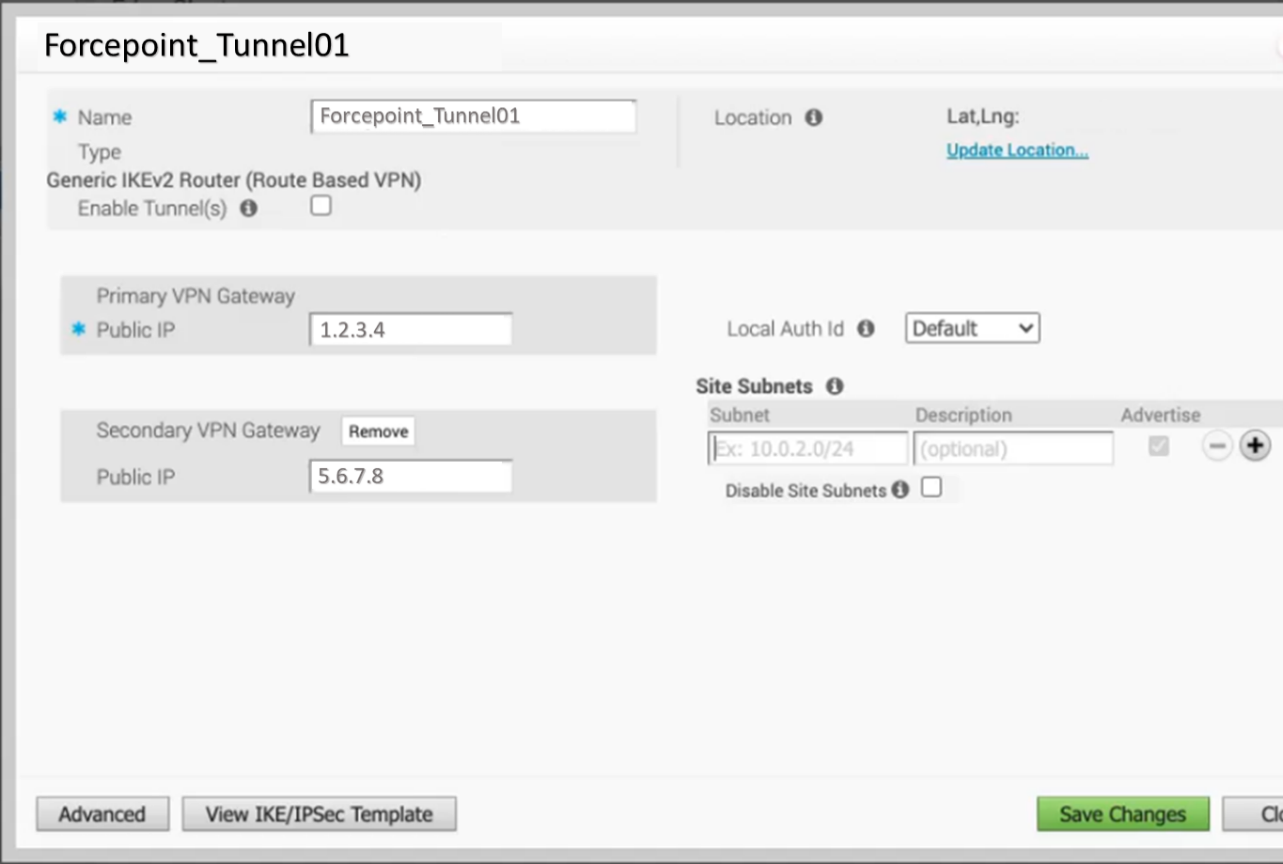
-
In the Advanced view fill or select the correct settings
-
Enable Tunnel(s): tick this box
-
PSK: the pre-shared key used when configuring the Edge Device in the previous chapter. In our example we used Velocloud321.
-
Redundant Tunnel PSK: same as before
-
Encryption: select AES-256
-
PFS: select disabled
-
Authentication algorithm: select SHA_256
-
Local Auth ID: select FQDN and enter the DNS name used when configuring the Edge Device in the previous chapter. In our example we used test.customer02.com
-
Disable Site Subnets: tick this box
-
Redundant VeloCloud Cloud VPN: tick this box, 2 tunnels each gateway will be set up
-
-
Leave all other settings as default then click Save Changes.
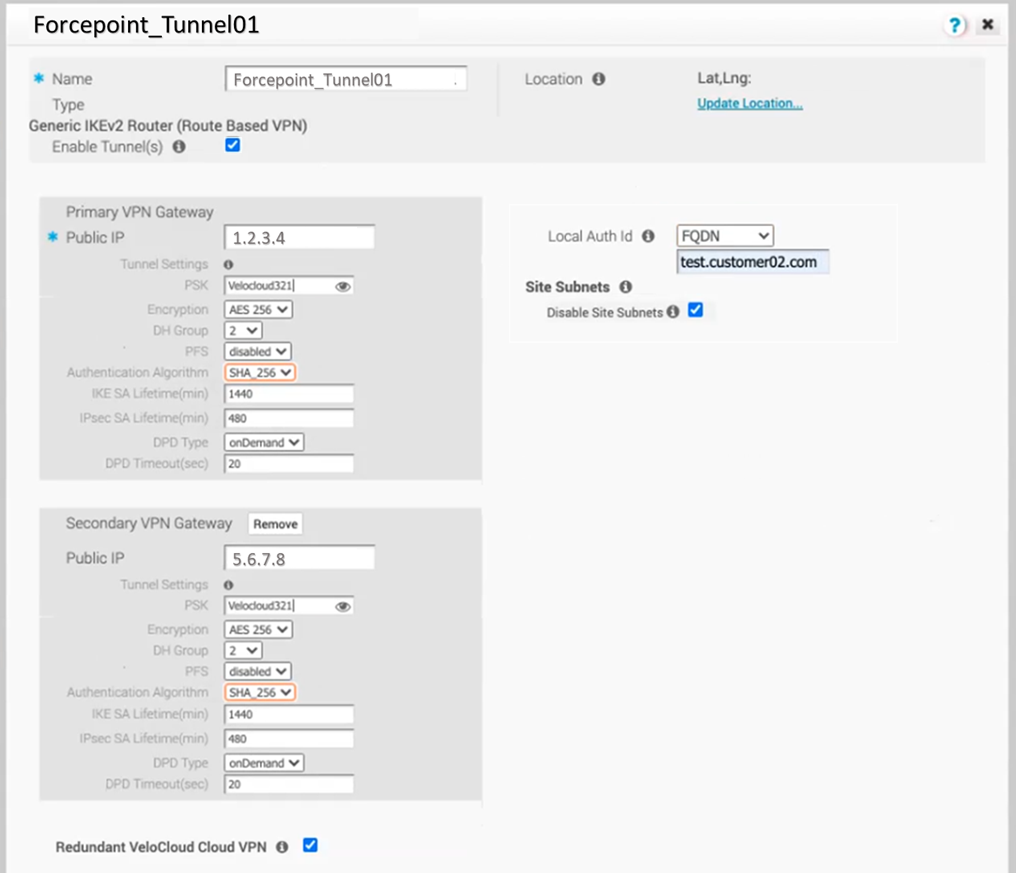
Once the new Gateway is created, it will be displayed in the Network Services page
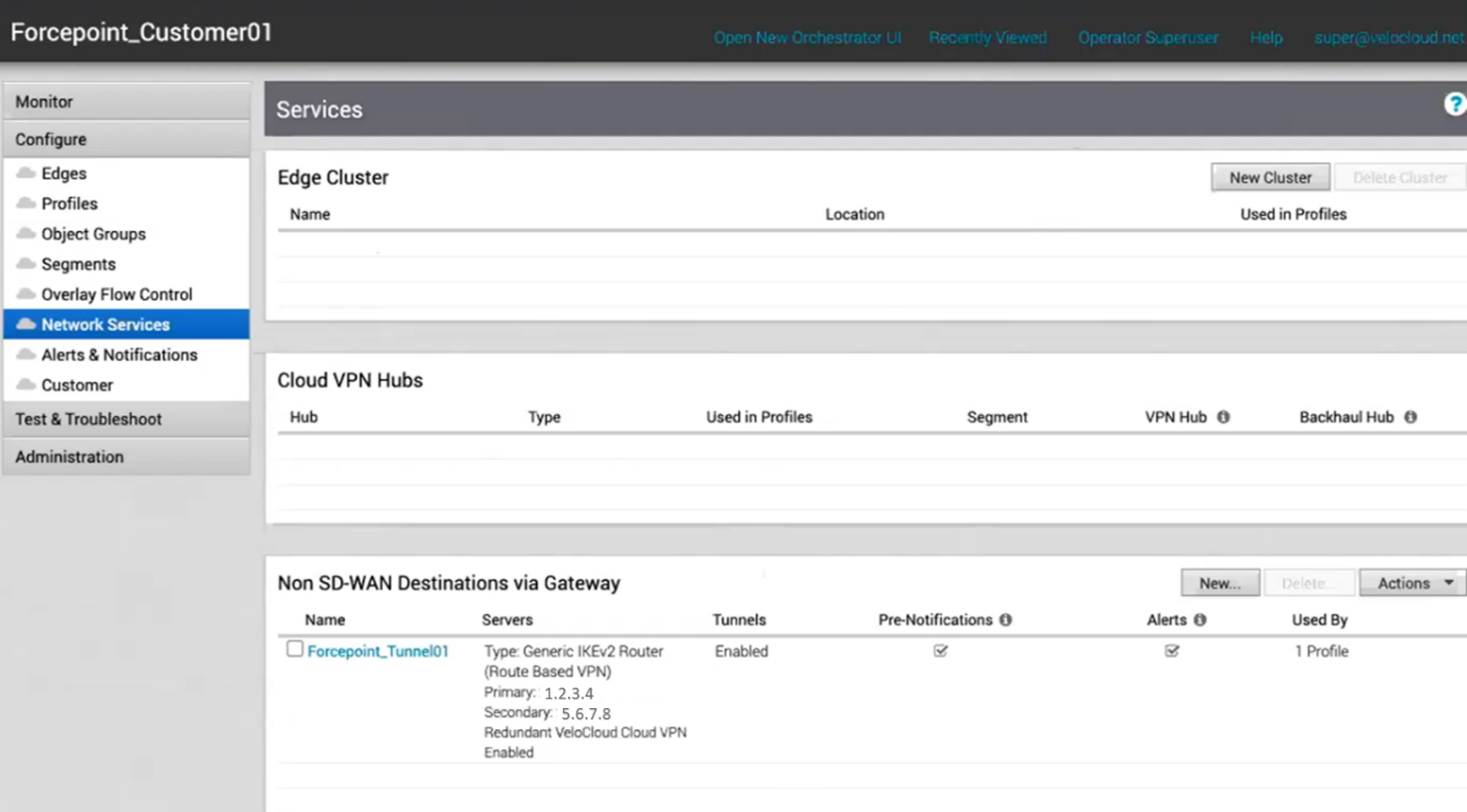
Configure a Profile with the new Gateway
An existing Customer configured inside VeloCloud Orchestrator is typically assigned with one or more Configuration Profiles.
This configuration element is needed to steer web traffic to Forcepoint Cloud Security Gateway.
- In the VeloCloud Orchestrator UI click Configure > Profiles and then click on the Profile that will be used for the Customer whose traffic will be sent to Forcepoint Cloud Security Gateway.
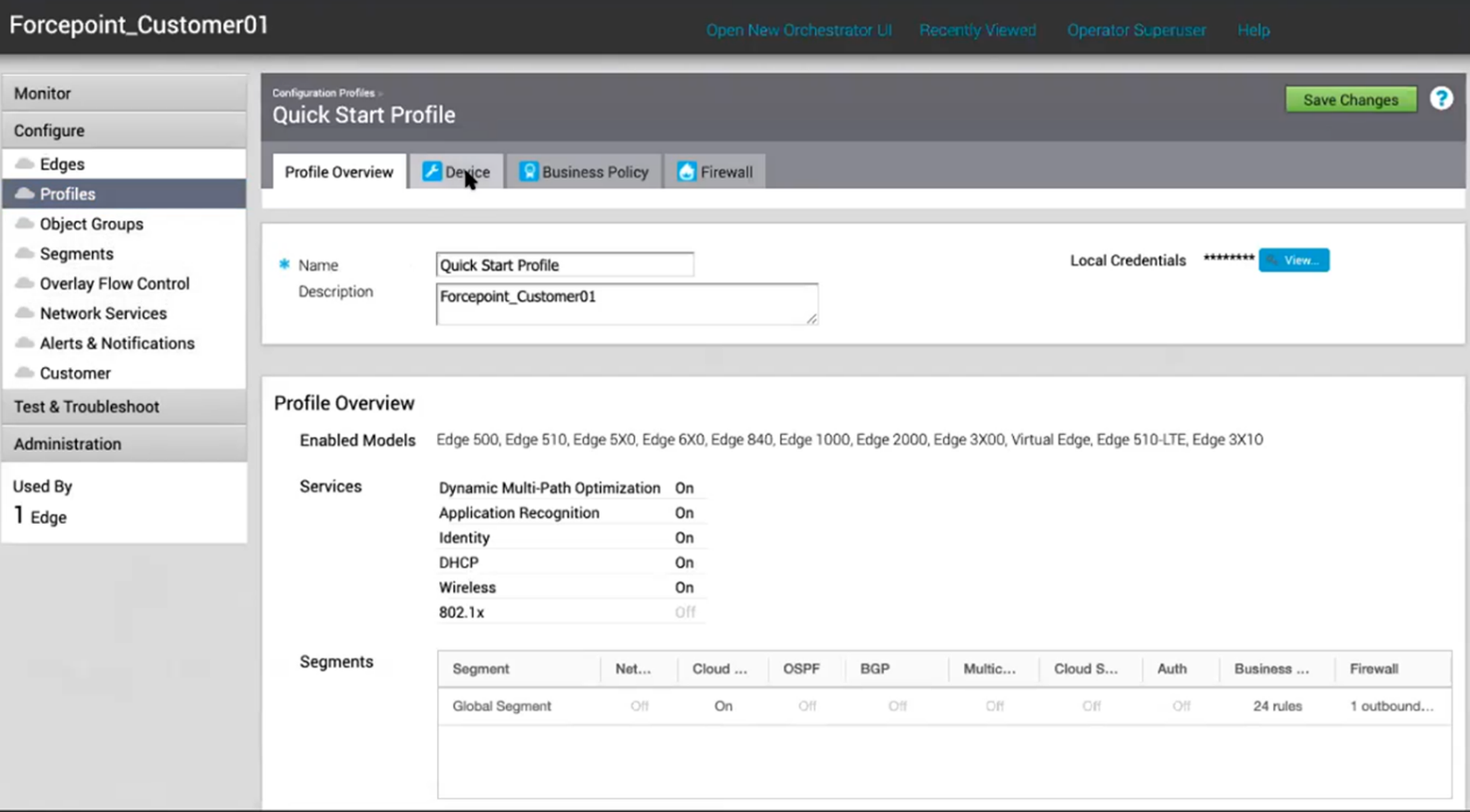
- Click Device tab and enable Cloud VPN moving the switch to the On position
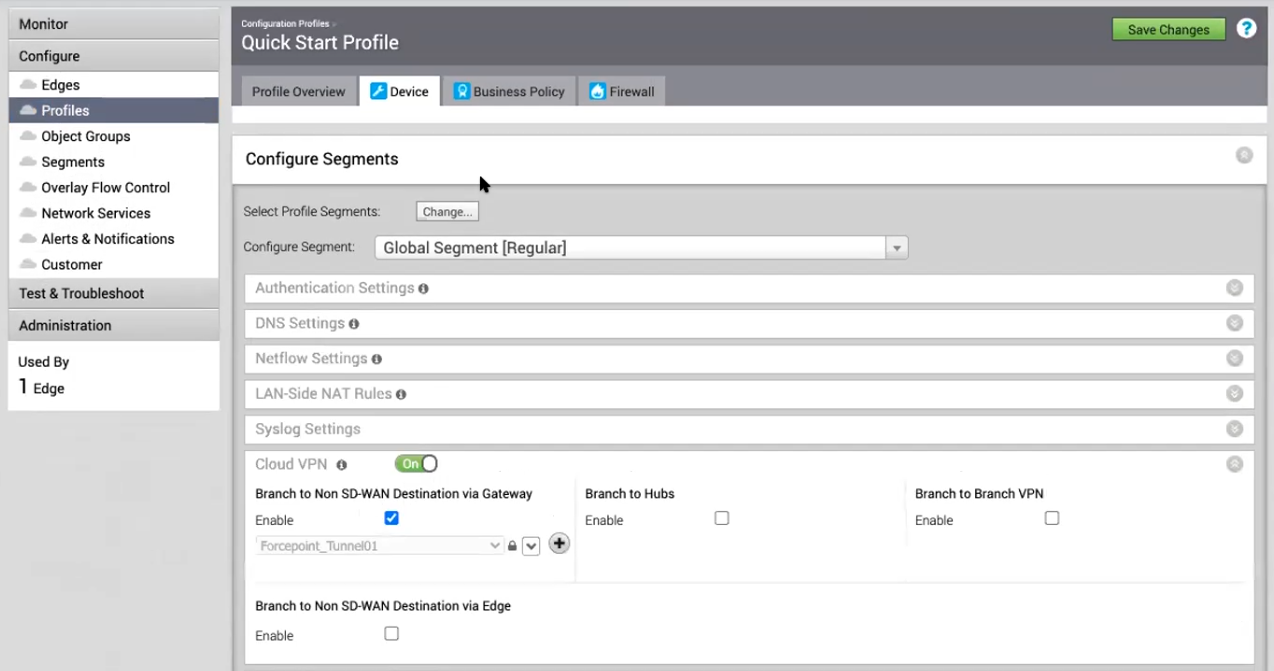
-
Under Branch to Non SD-WAN Destination via Gateway tick the Enable box to activate the drop-down menu and select the NSD Tunnel via Gateway previously created. Click Save Changes once done.
-
Move to the Business Policy tab and click New Rule…
-
In the Configure Rule window use the following settings
-
Rule Name: use a descriptive name
-
Source: leave Any to have all traffic from the Customer included in this policy
-
Destination: click Define… then pick Internet
-
Application: leave Any to steer all Internet traffic, or click Define… > Web > All Web to steer only http/https traffic
-
Priority: click High
-
Network Service: click Internet Backhaul then click Non SD-WAN Destination via Gateway and select the Gateway device created in the previous paragraph
Click OK once done.
-
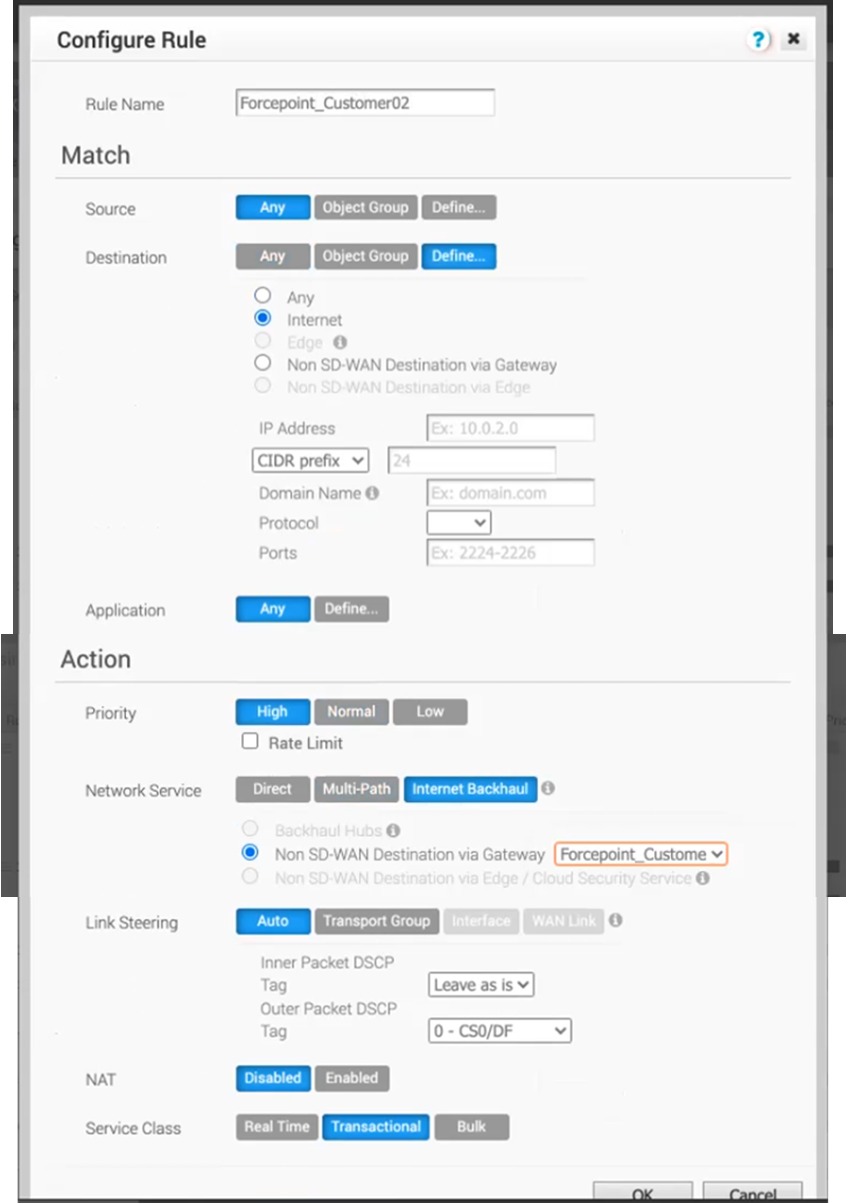
Configure VeloCloud Orchestrator - Edge
This chapter contains instructions to configure all components of the SD-WAN layer of VeloCloud Orchestrator using an Edge as the endpoint for the tunnels between VeloCloud and Forcepoint Cloud Security Gateway. It is assumed that a Customer is already configured.
Create new NSD Tunnel via Edge
- Login to VeloCloud Orchestrator using an account with administrative privileges
- Click Manage Customers then click the Customer whose traffic will be route to Forcepoint Cloud Security Gateway

-
Click Configure > Network Services then move to the Non SD-WAN Destinations via Edge and click New…
-
in the New Non SD-WAN Destinations via Edge window enter the following parameters:
-
Name: a descriptive name for the Edge
-
Type: select Generic IKEv2 Router
-
Primary VPN Gateway: fill this field with the primary IP address of your VeloCloud Edge device
-
Secondary VPN Gateway: fill this field with the secondary IP address of your VeloCloud Edge device, if available
-
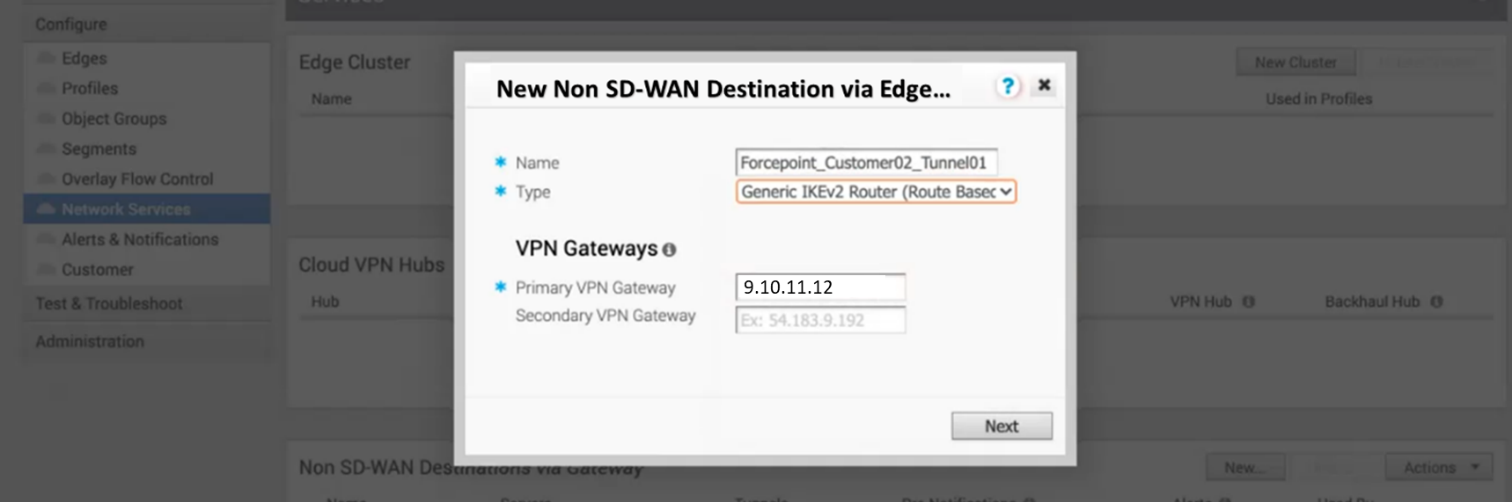
-
Once done click Next. The Edge will be created within a few seconds.
-
In the next window click Advanced.
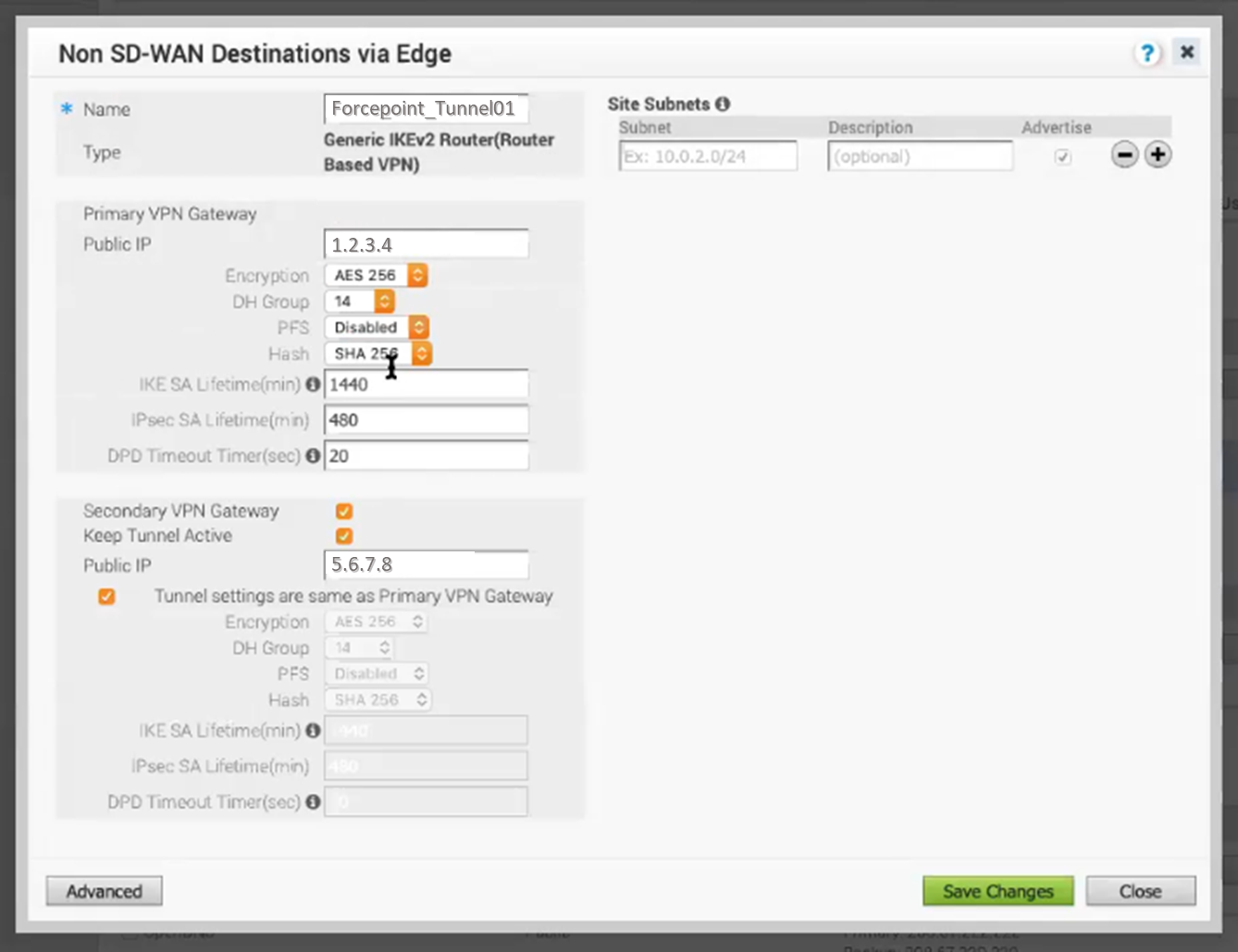
-
In the Advanced view fill or select the correct settings
-
Encryption: select AES-256
-
DH Group: 14
-
PFS: select disabled
-
Hash: select SHA 256
-
Tunnel settings are same as Primary VPN : tick this box, 2 tunnels each Edge will be set up
-
-
Leave all other settings as default then click Save Changes.
Once the new Edge is created, it will be displayed in the Network Services page
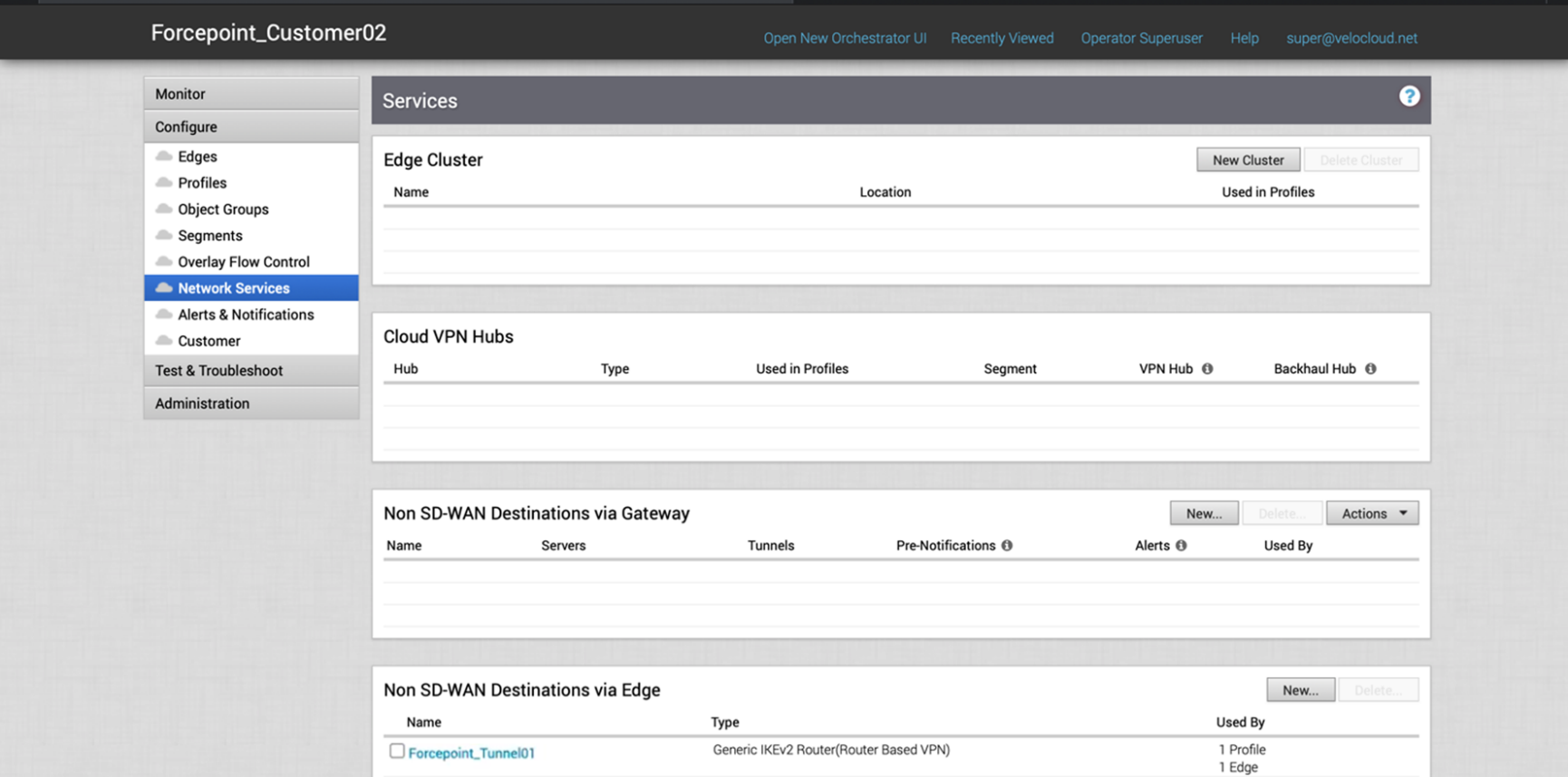
Configure a Profile with the new Gateway
An existing Customer configured inside VeloCloud Orchestrator is typically assigned with one or more Configuration Profiles.
This configuration element is needed to steer web traffic to Forcepoint Cloud Security Gateway.
-
In the VeloCloud Orchestrator UI click Configure > Profiles then click the Profile that will be used for the Customer whose traffic will be sent to Forcepoint Cloud Security Gateway.
-
Click Device, turn on Cloud VPN and enable the Branch to Non-SD-WAN via Edge option. Here we will select the Tunnel from Edge configured in the previous step.
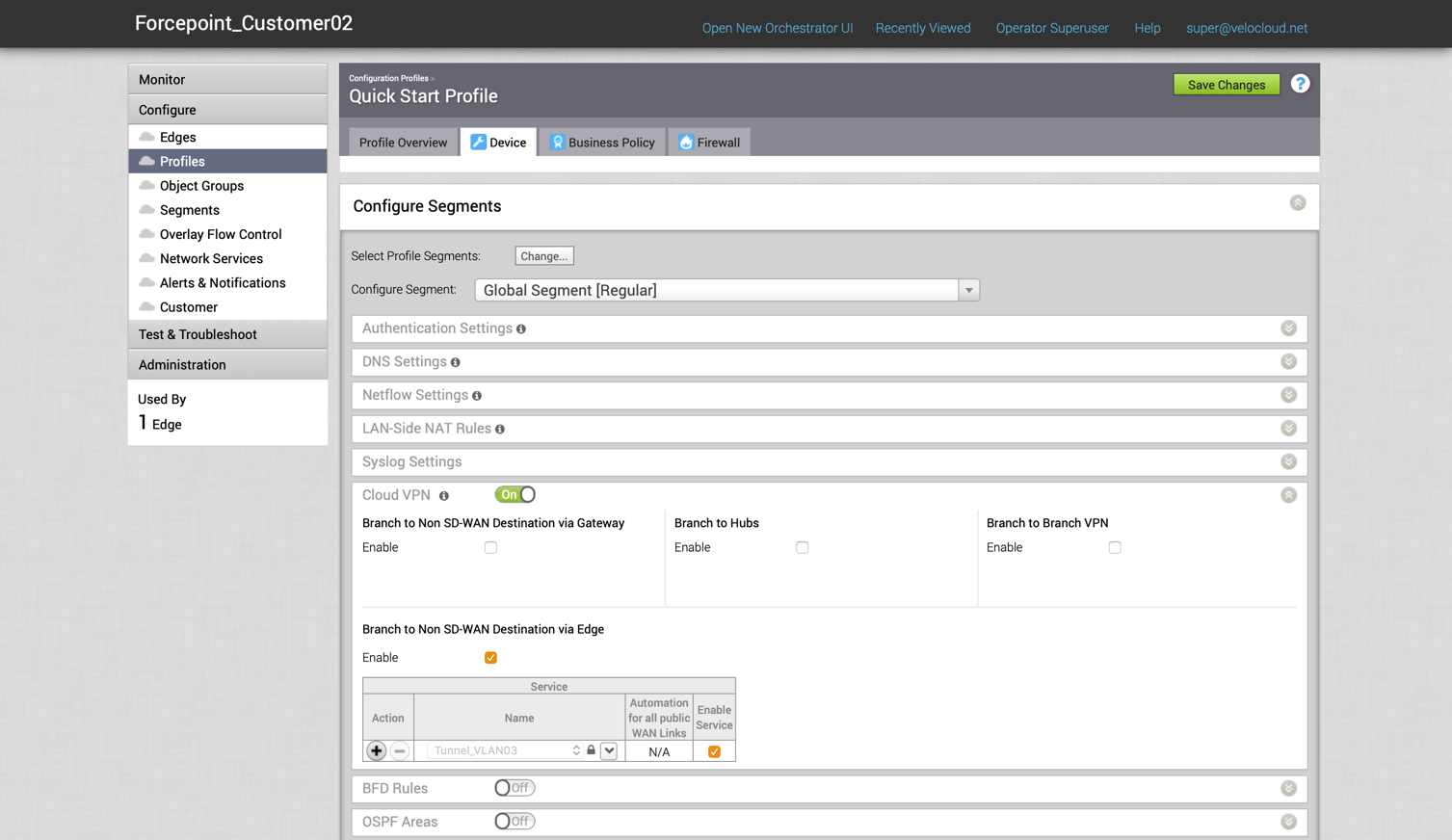
-
Move to the Business Policy tab and click New Rule…
-
In the Configure Rule window use the following settings
-
Rule Name: use a descriptive name
-
Source: leave Any to have all traffic from the Customer included in this policy
-
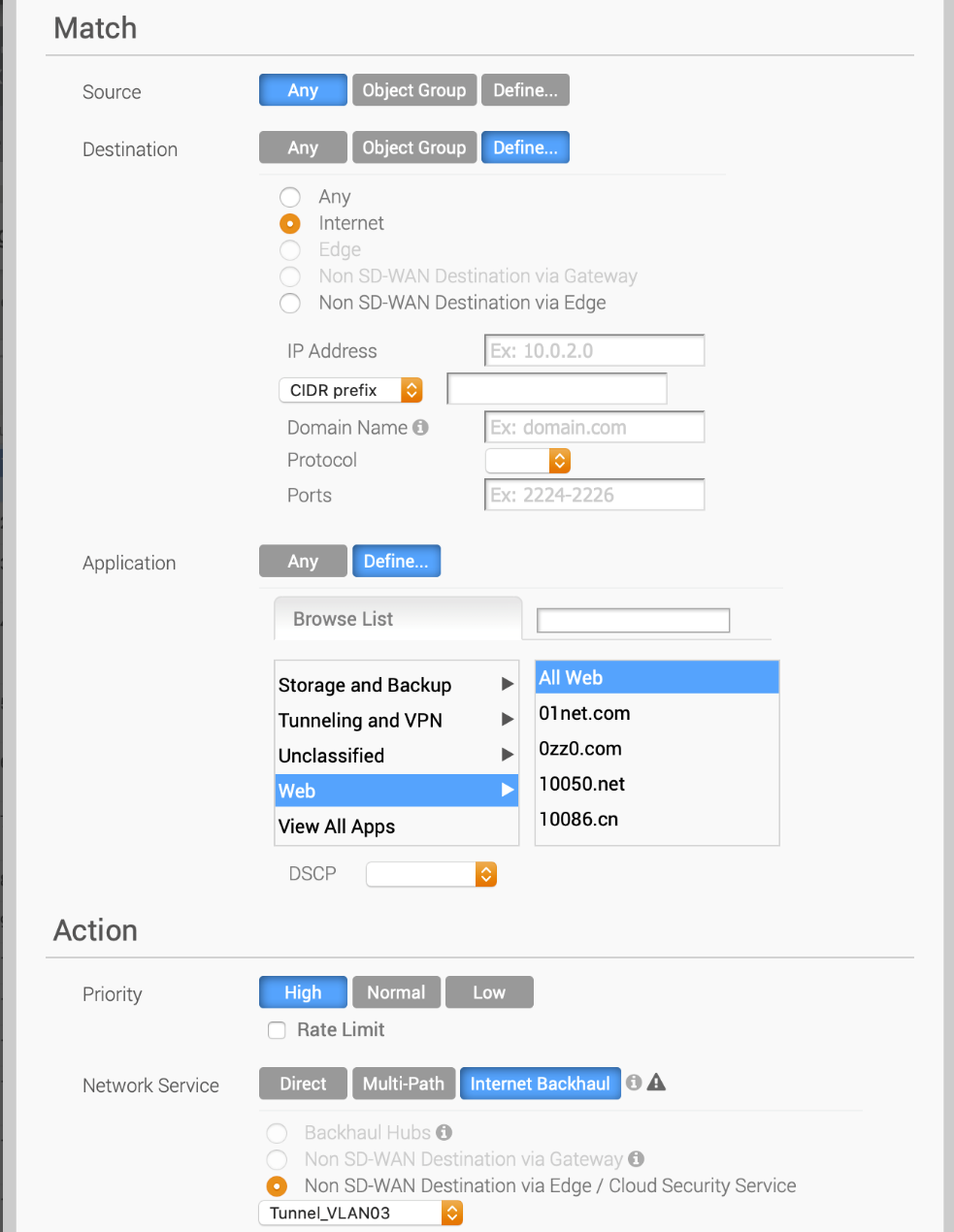
Destination: click Define… then pick Internet
-
Application: leave Any to steer all Internet traffic, or click Define… > Web > All Web to steer only http/https traffic
-
Priority: click High
-
Network Service: click Internet Backhaul then click Non-SD-WAN Destination via Edge and select the Gateway device created in the previous paragraph
Click OK once done.
-
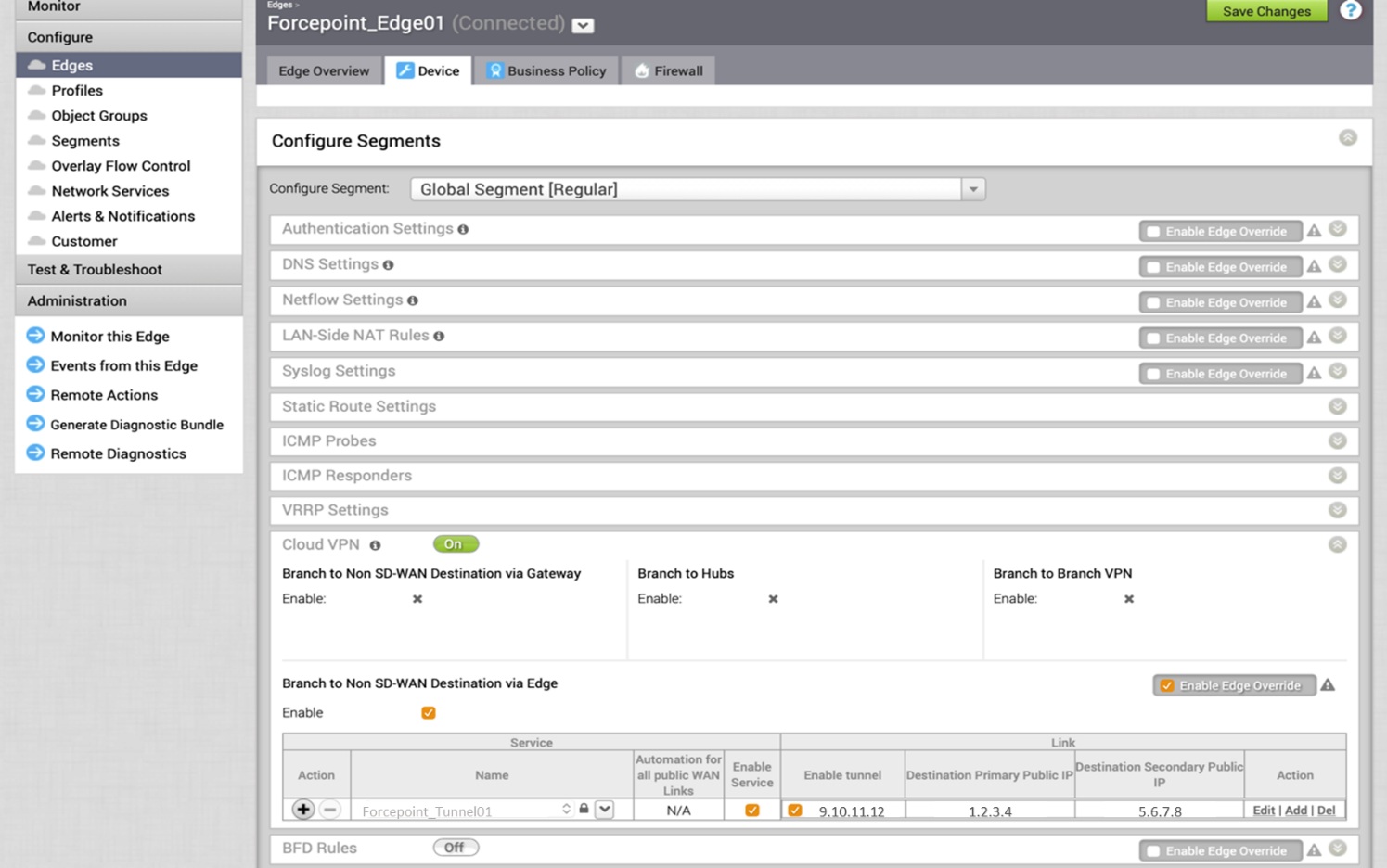
- As a final step, navigate to Configure > Edges > Device tab. Under the Cloud VPN section, configure the parameters as shown below.
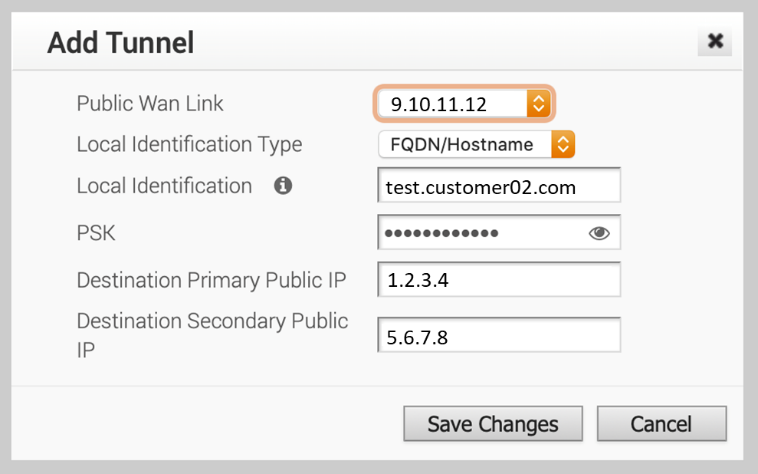
This is where the FQDN will be configured and the source of the tunnel will be chosen as the WAN IP address:
-
Public Wan Link: select the IP address of the VeloCloud Edge device hosting the Tunnel endpoint connecting to Forcepoint Cloud Security Gateway
-
Local Identification Type: select FQDN/Hostname
-
Local Identification: enter the same FQDN configured as the IKE Identity in the Forcepoint Cloud Security Gateway configuration
-
PSK: enter the same Pre-Shared Key configured in the Forcepoint Cloud Security Gateway configuration
-
Destination Primary Public IP and Destination Secondary Public IP: enter the Service IP addresses of the datacentres obtained in the Forcepoint Cloud Security Gateway configuration
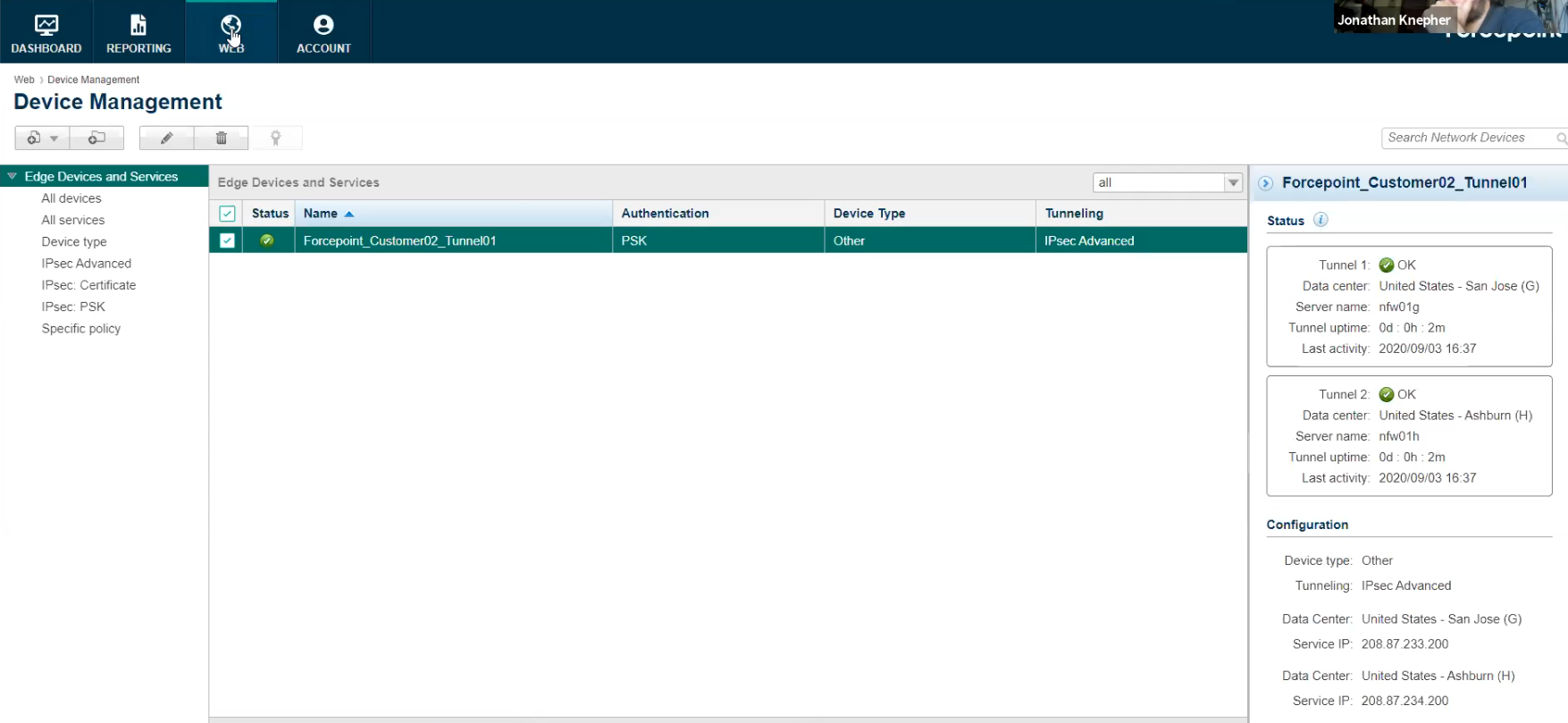
Check status of IPSEC tunnels
Once both Forcepoint and VMware sides are configured, it will take a few minutes before IPSEC tunnels are set up and established. Tunnels status can be checked on both sides.
-
In Forcepoint Cloud Security Gateway, go to Device Management > Edge Devices and Services and click on the Edge Device configured for this integration.
If the tunnels are set up correctly, both Tunnels will show up a green icon and display details of the connections. Note that each tunnel will display green if at least one of the redundant connections from VeloCloud is active.
-
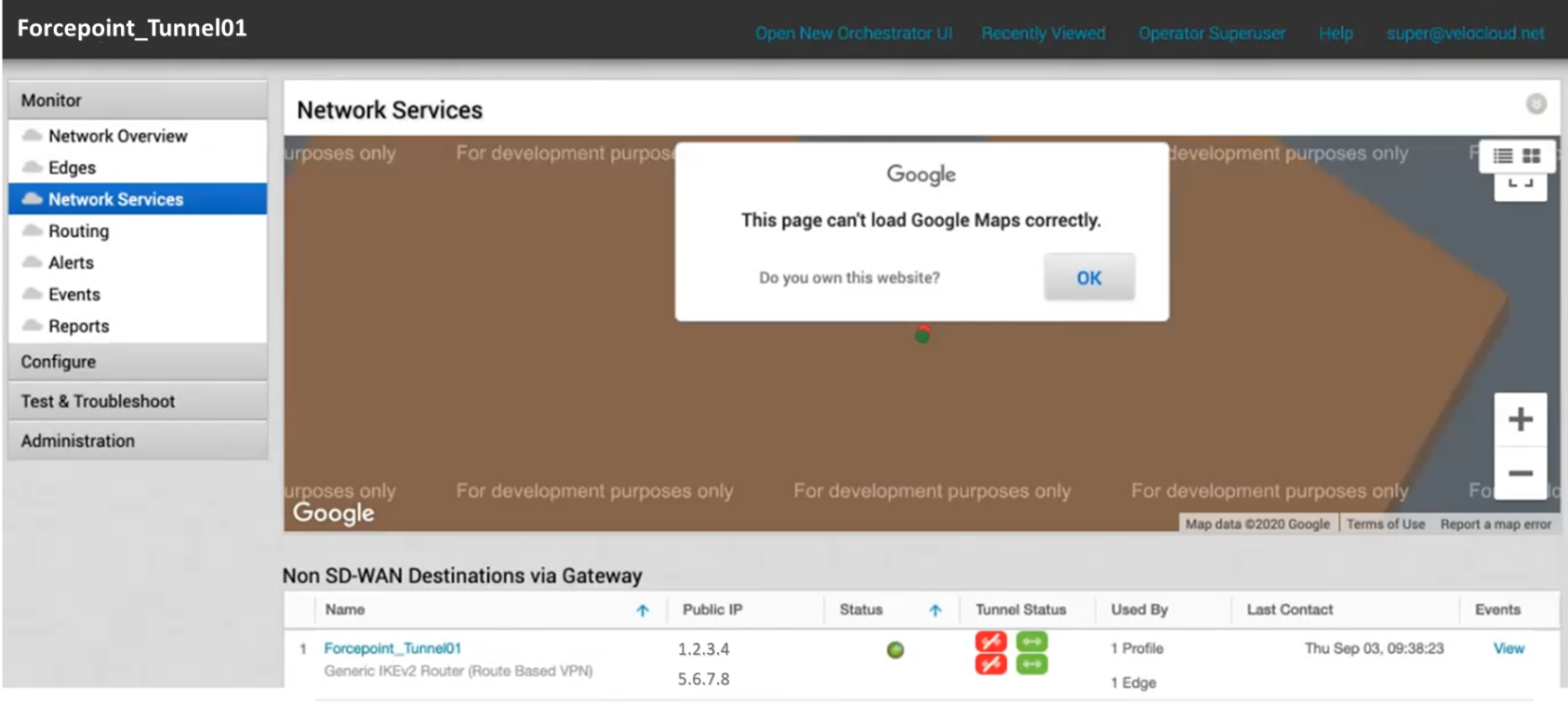
In VeloCloud Orchestrator, go to Monitor > Network Services: each Forcepoint data center will be the endpoint of redundant IPSEC tunnels.
Status of Non SD-WAN Destinations via Gateway .
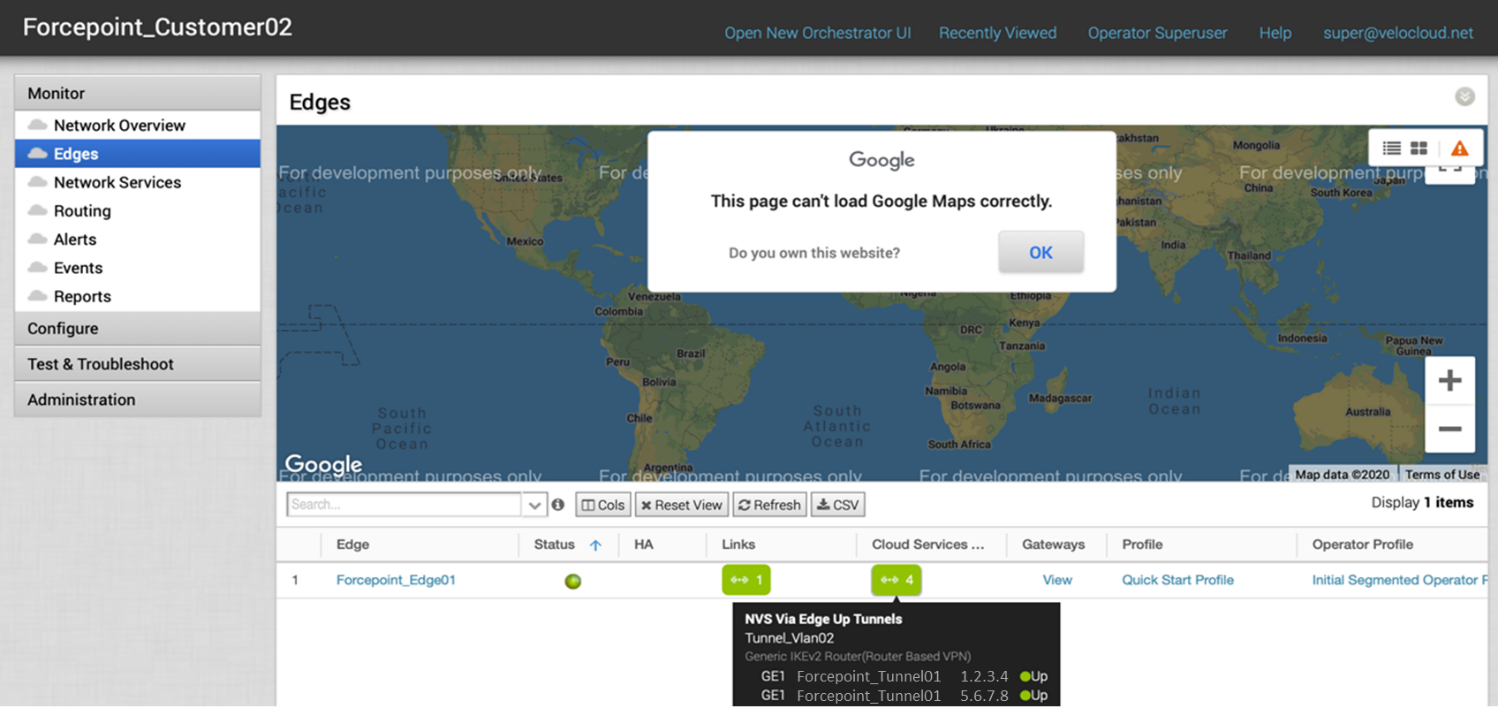
Status of Non-SD-WAN Destinations via Edge
Validate integration end to end
Once both Forcepoint Cloud Security Gateway and VMware SD-WAN by VeloCloud are configured, end to end validation is possible by browsing a disallowed website (based on the security policy configured in Forcepoint Cloud Security Gateway) from a machine connected to the SD-WAN.
- Using a machine connected to the SD-WAN, open a browser and navigate to a website belonging to a category blocked by the security policy assigned to the Edge Device used for the integration with VMware SD-WAN by VeloCloud.
If the integration is configured correctly and the security policy is configured to display a block notification, the browser will display a message similar to the following.
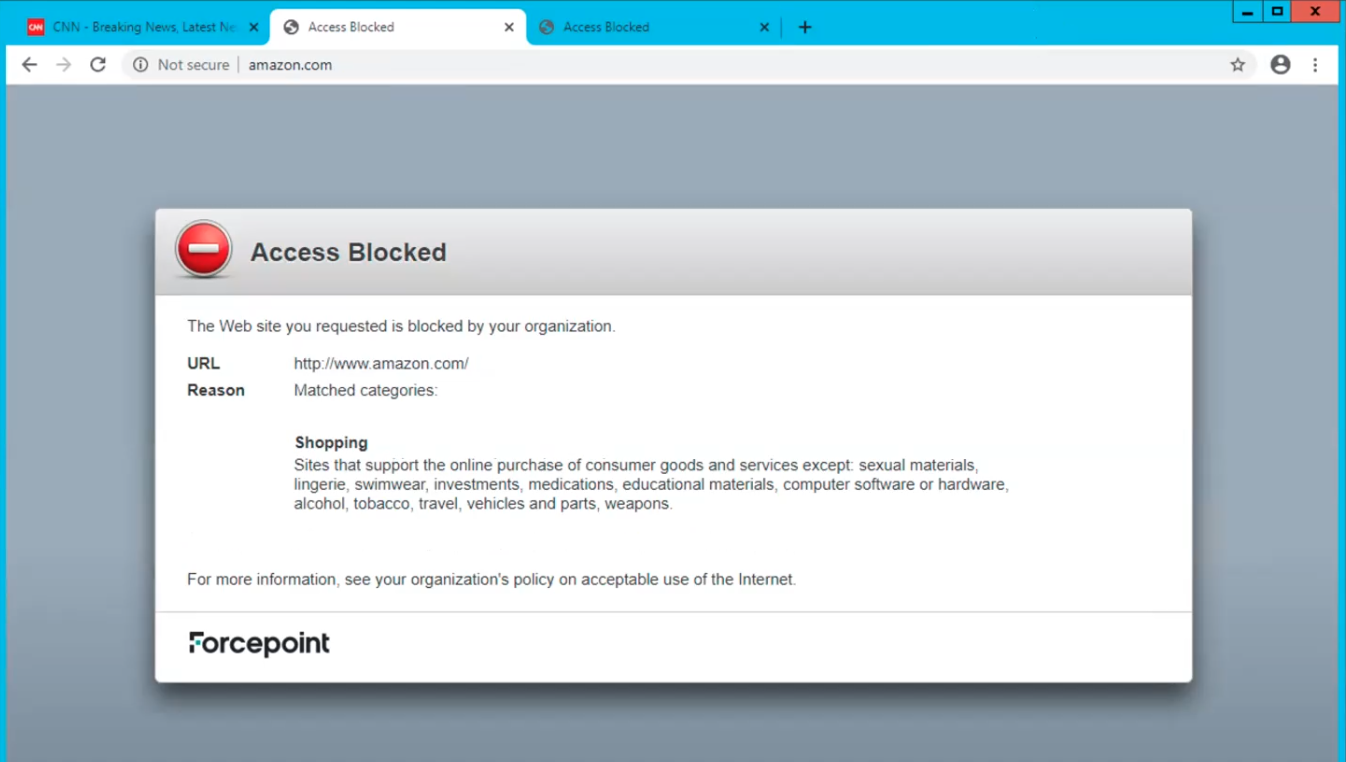
This block page demonstrates that the user traffic has been correctly tunnelled to Forcepoint Cloud Security Gateway and web security policies were enforced successfully